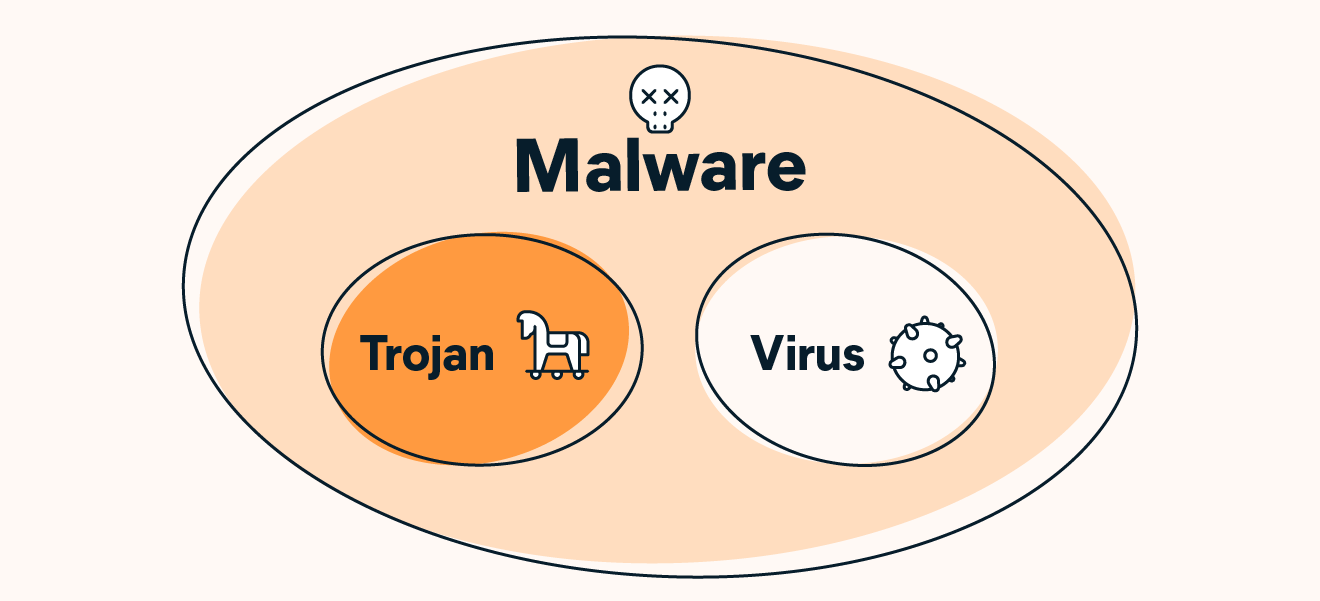
Product code: Effects of trojan horse 2025 malware
How Trojan Horse Malware Effects On Computers Ransomware 2025, Trojan Horse Meaning Examples Prevention 2025, What is a Trojan Virus Trojan Horse Malware Imperva 2025, What are Trojan Viruses and How Do These Threats Work Top Cloud 2025, What Is a Trojan a Virus or Malware How Does It Work Avast 2025, What is a Trojan How this tricky malware works CSO Online 2025, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus 2025, What are Trojan Viruses and How Do These Threats Work Top Cloud 2025, Demystifying Trojans A Comprehensive Guide to Understanding 2025, Trojan Horse Meaning Examples Prevention 2025, What is Trojan Horse Computing zenarmor 2025, Trojan horse removal Protecting Troy 2025, What is a Computer Trojan Identifying Protecting Virus 2025, What Is a Trojan a Virus or Malware How Does It Work Avast 2025, The Difference Between a Computer Virus Worm Trojan Horse 2025, What is a Trojan Horse Virus Types and How to Remove it 2025, Trojan Attacks How Does Trojan Horse Infect Devices 2025, Frontiers The Trojan Horse Model in Paracoccidioides A 2025, What Are Trojans How Can You Protect Yourself 2025, The Trojan Horse Goes Wild The Effect of Drug Loading on the 2025, What is a Trojan Horse U.S. News 2025, Trojan Horse The UTSA CIAS 2025, Trojan Horse Plurilock 2025, What is a Trojan Horse Virus Definition Examples Removal Options Video 2025, What is a Trojan Virus Trojan Horse Virus Box Inc 2025, Botnet concept. Robot network malware attack. stock video 1483126451 2025, Trojan Horse Virus History Types and Working 2025, How to Tell if Your Computer Is Infected by a Trojan Horse 2025, Trojan Malware Unveiled All You Need to Know to Stay Safe 2025, trojan horse virus computer destroys laptop 2315560 Vector Art at 2025, What is a Trojan Malware and How Does It Work EasyDMARC 2025, Trojan Virus Unmasked What You Need to Know Silent Quadrant 2025, What are the Characteristics of a Trojan Malware 2025, Effects of Zeus Malware GeeksforGeeks 2025, Virus malware routes in mobile devices Download Scientific Diagram 2025.
How Trojan Horse Malware Effects On Computers Ransomware 2025, Trojan Horse Meaning Examples Prevention 2025, What is a Trojan Virus Trojan Horse Malware Imperva 2025, What are Trojan Viruses and How Do These Threats Work Top Cloud 2025, What Is a Trojan a Virus or Malware How Does It Work Avast 2025, What is a Trojan How this tricky malware works CSO Online 2025, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus 2025, What are Trojan Viruses and How Do These Threats Work Top Cloud 2025, Demystifying Trojans A Comprehensive Guide to Understanding 2025, Trojan Horse Meaning Examples Prevention 2025, What is Trojan Horse Computing zenarmor 2025, Trojan horse removal Protecting Troy 2025, What is a Computer Trojan Identifying Protecting Virus 2025, What Is a Trojan a Virus or Malware How Does It Work Avast 2025, The Difference Between a Computer Virus Worm Trojan Horse 2025, What is a Trojan Horse Virus Types and How to Remove it 2025, Trojan Attacks How Does Trojan Horse Infect Devices 2025, Frontiers The Trojan Horse Model in Paracoccidioides A 2025, What Are Trojans How Can You Protect Yourself 2025, The Trojan Horse Goes Wild The Effect of Drug Loading on the 2025, What is a Trojan Horse U.S. News 2025, Trojan Horse The UTSA CIAS 2025, Trojan Horse Plurilock 2025, What is a Trojan Horse Virus Definition Examples Removal Options Video 2025, What is a Trojan Virus Trojan Horse Virus Box Inc 2025, Botnet concept. Robot network malware attack. stock video 1483126451 2025, Trojan Horse Virus History Types and Working 2025, How to Tell if Your Computer Is Infected by a Trojan Horse 2025, Trojan Malware Unveiled All You Need to Know to Stay Safe 2025, trojan horse virus computer destroys laptop 2315560 Vector Art at 2025, What is a Trojan Malware and How Does It Work EasyDMARC 2025, Trojan Virus Unmasked What You Need to Know Silent Quadrant 2025, What are the Characteristics of a Trojan Malware 2025, Effects of Zeus Malware GeeksforGeeks 2025, Virus malware routes in mobile devices Download Scientific Diagram 2025.